Introducing the Line of Trust (LOTr)
Erasing the line of death for fun and pleasure
Motivation
The Line of Death (LoD) is a class of web browser attacks that target the very pixels of a browser UI on a given webpage, especially with regards to the (presumably) browser-controlled portion of the UI above webpage content.
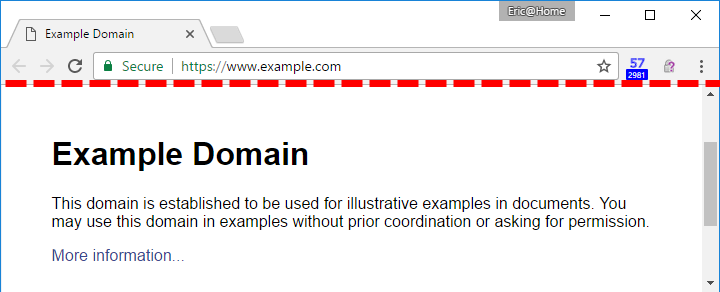
LoD attacks span the spectrum from manipulating URL names and tabs to spoofing new browser windows within the webpage’s content area:
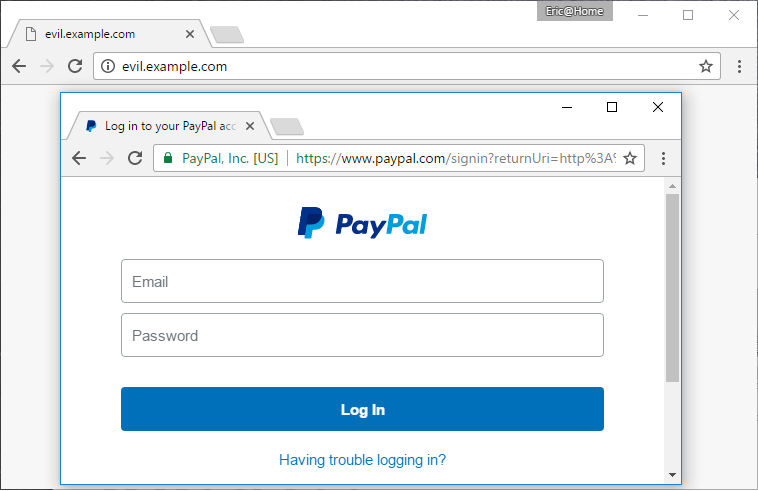
Certified Malice is a phishing attack that deceives users into trusting a page that looks nearly identical to the real site, including TLS certificates with realistic naming schemes. This threat becomes even more potent if combined with URL pixel manipulation.
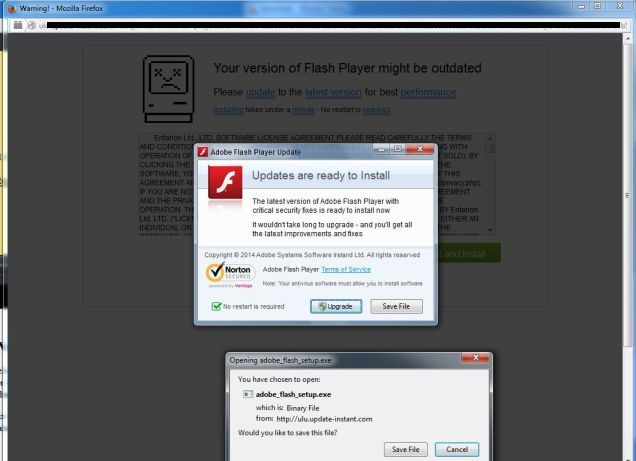
LoD attacks encompass more than just browser-object and URL spoofing attacks. Some attacks attempt to erode users’ abilities to discern legitimate OS prompts from spoofed prompts displayed in the browser, often designed to scare users into downloading or updating software.
Given the broad range of LoD-inspired attacks that have surfaced in the past year, the Line of Trust project seeks to improve the level of security a browser provides when trusted UI pixels and browser notifications are compromised or forged.
Goals for Line of Trust
Specifically, we are interested in developing baked-in browser warnings for content that is suspected to be a LoD attack. We will be using Google Chromium to develop LOTr.
Our overarching goal is to reduce the feasibility of LoD attacks while providing increased transparency to the end-user. We are currently considering various computer vision techniques to build LOTr.
Relevant Resources
News, Blogs, & Forums
The Line of Death - Hacker News
The Line of Death - Text/Plain
Contributors
- Anant Kharkar, undergraduate student at the University of Virginia
- Sam Havron, undergraduate student at the University of Virginia
- Bill Young, graduate student at the University of Virginia
- Joshua Holtzman, undergraduate student at the University of Virginia
- Dave Evans, project advisor and computer science professor at the University of Virginia